
Background information
After the Dropbox hack: the cloud in your own home
by Dominik Bärlocher

Fingerprint scanners are the quickest way to unlock your phone, but they are certainly not the most secure. Iris scanners carry even more of a security risk. Here, we give you the low-down on the role your finger plays in security, Switzerland’s take on the legal side of things and why the peace sign can jeopardise your security.
These days, fingerprint technology is the established way to unlock smartphones. Devices without such a scanner seem old-fashioned or technologically inferior. But experts in the field of information security are horrified when they think about the advances in biometric data as an authentication factor. The term ‘biometric data as an authentication factor’ is pretty useless anyway, as no one understands it. This is what it really means:
In this article, I’ll be talking about biometric data from fingerprints and occasionally from the iris. The reason I’m mentioning both is that all arguments for and against fingerprints can, with a bit of thought, apply to the iris as well.
On TV and in films it’s easy to fake a fingerprint. You just need a bit of powder and sticky tape. Sometimes even wax and face powder will do the job. But surely it’s not as straightforward as that in real life, is it?
That’s right, because you definitely need a bit of time and a DIY store (or just trusted Galaxus). Hacker Jan Kirssler, alias Starbug from Chaos Computer Club, is the expert when it comes to faking fingerprints. In one particular video he demonstrates how he leverages an iPhone’s biometric sensor with the simplest means.
The problem is not just that fingerprints are relatively easy to leverage. There is also the issue of threat analysis. Experience has shown that threat analysis is something many companies and private users treat as secondary in importance. They often mention Russian hackers and Chinese state hacking without really giving it much thought. In everyday terms, that is like saying “But I don’t have anything to hide” or “Who wants my photos anyway?”. Most people don’t give it a moment’s thought or stop to consider what might get damaged if they were hacked.
Essentially, a threat analysis is the well-researched answer to the question “What happens if a security measure fails?”. For example, what if a fingerprint is faked? This is closely followed by questions like “What happens if all my photos in iCloud or my Google Drive are made public?” Do you really mean to say that wouldn’t be embarrassing? My colleague recently mentioned the time when she had naked photos of herself on Google Drive. They were only intended for her boyfriend but Google was nice enough to copy them to her Drive via Photos App.
Fingerprint technology allows anyone to access those naked selfies on your iPhone. Is that something you want? “Definitely not!” my colleague exclaimed. There you go. Threat analysis. “Well, I wouldn’t be too bothered about photos of me in my underwear being published. Because they were already staged and everything. But the photos I took to help me with my diet… that would be embarrassing,” she added.
The good news is that my colleague’s ‘in the buff’ problem can be easily solved.
Now that we know it’s possible to falsify a fingerprint with wood glue and we’ve thought about where and how it can be accessed and by whom, we’re ready for the next step.
A password is a dynamic object. That means that you can change it as often as you need to. It doesn’t matter if you have 123456, yA3XKdpa or CorrectBatteryStapleHorse as a password. What is important is that you can change it as often as you want. You can change your password strategy or even the length, numbers and punctuation marks. It only takes a few seconds.
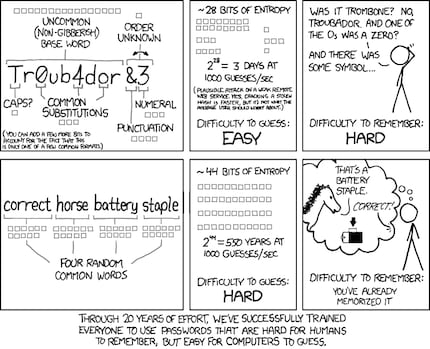
Original by Randall Monroe/xkcd
It’s not the same story when it comes to your fingerprints. You only get 10 fingerprints, which have to last you a lifetime. Bear in mind that they don’t normally change. Now imagine your fingerprint were stolen – you would always have a security issue. Should the attacker go to the effort of stealing all your fingerprints then this authentication method is over for you.
If you still want to use a touch sensor, you’re asking for esoteric solutions. You have 10 toes you could still scan, and you have two eyes for the iris scanner. On a less serious note, men have another option. Ladies, I’m afraid this one isn’t open to you.
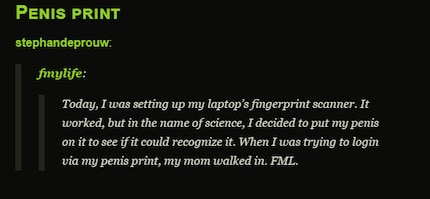
And yes, that does actually work
What started as a joke lead to research and Reddit User tested various different body parts.
In the video above, attackers need to have your smartphone. Whether they steal it or briefly borrow it is of no relevance, as demonstrated by hacker Starbug’s new attack. He can capture fingerprint data from a decent, high-definition photograph and then recreate it using the technology shown above.
This is what he did two years ago. The Japan Times recently disclosed that there are now new and shocking ways of capturing biometric data. Researchers at Japan’s National Institute of Informatics (NII) were able to recreate fingerprints in laboratory conditions. They managed to capture data when they were three meters away from their target. To put this in context, Starbug used a photograph of German Defence Secretary Ursula von der Leyen from the Internet and got his tools from a DIY store. His research showed he could capture fingerprint data for authentication from a distance of seven meters.
However, the focus of the Japan Times wasn’t on photographs that can be used to extract fingerprints. Instead, this was the key takeaway from their article:
But NII says it has developed a transparent film containing titanium oxide that can be attached to fingers to hide their prints, the reports said.
The risk of being photographed by HD cameras and having fingerprints stolen seems to be so great that Japan is now researching and discovering countermeasures.
As far as security goes, you can be forced to unlock your smartphone using fingerprint technology, but you don’t have to divulge a password. Just saying ;).
This is the comment user bluefisch200 left in response to my article on Speed tuning for Android. When I asked for a source, bluefisch200 sent me a link to online magazine Mashable, which reported that an American judge was the first to legally rule on classifying and differentiating fingerprints:
Bluefisch200 concluded that the same applies in Switzerland.
“That is not the case“, says Martin Steiger, a lawyer at a law office in Zurich, who specialises in digital cases. He found the precedent in the US fascinating but explained that it did not directly apply to Swiss law. This means that the US precedent can’t automatically be used in similar cases in Switzerland.

Swiss police can’t force you to unlock your phone. Image: Kapo ZH / Facebook
On the contrary: “No one is obliged to unlock their phone if they are asked to, whether by using a password or fingerprint technology”, says Steiger. Even a search warrant could be contested. However, Steiger is not as yet aware of any fingerprint cases in Switzerland. He assumes that the country’s law enforcement agencies have already considered this. Explaining further, he says that if the police captured a ‘voluntarily’ unlocked phone, the evidence could not necessarily be used in court.
The situation is similar when it comes to taking fingerprints. The police are allowed to take your fingerprints, but you can refuse. With the relevant decision, the public prosecutor’s office can later request your fingerprints as a coercive measure. However, according to Steiger, even once the police have successfully taken fingerprints, they are not allowed to use them to unlock a phone. This is as far as Starbug’s method can go. “However, the rule of law in Switzerland often adopts a ‘the end justifies the means’ approach. This is why I would not be surprised if a dummy finger for unlocking devices were permitted by law”, says Steiger.
But the lawyer warns that "The police often ask defendants for their passwords and PIN during their first contact. Or later on they may ask them to unlock the phone using fingerprint technology." But these questions don’t have to be answered. When in doubt, defendants should at the very least refuse to give information and not unlock their phone. Steiger explains that they don’t need to give a reason, as the maxim “No person is to be compelled to accuse themselves” applies in a constitutional state.
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all