
Background information
WhatsApp security breach - researchers find backdoor, Facebook doesn't care
by Dominik Bärlocher

Does WhatsApp have a vulnerability or not? The answer: Yes and no. Because the vulnerability from last weekend is one that penetrates deep into the problems of cryptography in everyday life. The cryptographer behind the encryption explains.
Shortly after the talk by Tobias Boelter at the 33rd Chaos Computer Congress (33c3) attracted the attention of the mass media, the cryptographer and inventor of WhatsApp encryption talks about the problem. In addition to reassurances that this is not a backdoor, Moxie Marlinspike gives an insight into the work and problems of a cryptographer.
WhatsApp uses the Signal Protocol for encryption, which was invented by Open Whisper Systems. Open Whisper Systems is a company founded by cryptographer Moxie Marlinspike. Moxie Marlinspike, by the way, is not his real name, but in the InfoSec scene as well as the general public he is only known by this name. Marlinspike is also one of the co-authors of the encryption mechanism used by Signal (Android, Apple iOS and Chrome) and WhatsApp.

Marlinspike spoke out in a blog post on Whispersystems.org shortly after it went viral in the media. Under the title "There is no WhatsApp backdoor", he says that the Boelters exploit works and that it is expected behaviour, but that this is not a vulnerability per se. Rather, it is two problems of cryptography colliding.
In order to understand the blog post, you may need an explanation of what a "man in the middle" attack is. In short: Web traffic that is actually private is routed via third-party infrastructure where it is intercepted. In practice, it looks like this:
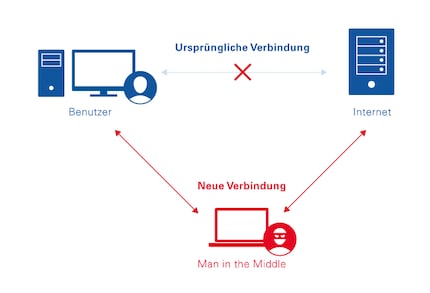
WhatsApp could try to "man in the middle" a conversation, just like with any encrypted communication system, but they would risk getting caught by users who verify keys.
German: WhatsApp could try a man in the middle attack on a conversation, just like with any encrypted communication system. But they would risk being caught by users verifying their keys.
This is because the WhatsApp server stores all kinds of personal and impersonal user data, but not whether the user is notified when a key changes. Marlinspike therefore assumes that a significant number of users verify their keys and do not blindly trust WhatsApp. This would be correct behaviour in itself and a change in the app's behaviour would be detected if the spying was systematic. It is also assumed that everyone who needs WhatsApp's cryptography also verifies their keys. But who does that in everyday life? And this is where convenience meets security. Communication would certainly be blocked and unreadable until my counterpart has verified my key. In the Signal Chrome plugin, screenshots are not allowed in the app, it looks like this.
The vulnerability described in my previous article and discovered by Tobias Boelter works, even if it relies on users not taking care of the encryption of the chat. Nevertheless, it comes with its limitations:
The WhatsApp clients have been carefully designed so that they will not re-encrypt messages that have already been delivered. Once the sending client displays a "double check mark," it can no longer be asked to re-send that message.
The WhatsApp clients have been carefully designed so that they do not re-encrypt messages that have already been received. As soon as the two tick marks are displayed on the sender's client, they can no longer be asked to resend the message.
Only semantically, Marlinspike argues that the backdoor reported by Boelters is not a backdoor. Nevertheless, anyone with access to WhatsApp's server can listen in on all future messages. However, past conversations cannot be read. So, backdoor functionality is present, even if it was not planned that way.
The attacker - in this case the main concern is the so-called three letter agencies in the scene, i.e. FBI, NSA, CIA, etc. - is therefore only able to read current and future messages.
In the comments to the previous article, I was repeatedly asked about other messengers. It would take far too long to answer each question individually. Nevertheless, it is important to me that you understand why I recommend Signal and not Threema, Wire or Telegram.
As far as I know, Signal is the only client that is completely open source. This means that anyone can view the entire code. Of course, only a fraction of users have the ability to check the code, but many experts rush to the code, compile it themselves and immediately report any vulnerabilities. Nowadays, vulnerabilities are often rewarded with bug bounties, i.e. money in exchange for vulnerabilities. Even if this is not the case, great importance is attached to these vulnerabilities when they are published. In the case of Signal, the code has actually been audited and, lo and behold, it does exactly what Open Whisper Systems promises. No more and no less. With other messengers, either parts or the entire system are closed source, which means you're buying a pig in a poke.
Speaking of buying: Signal is free. Open Whisper Systems keeps its head above water with donations and subsidies. Regardless of where these subsidies come from, they enable the developers to develop their product away from the profit motive. Should a backdoor or other vulnerability actually be discovered, or the server be compromised by a three-letter agency, the developers could simply pack up and call it a day. This is what happened with the encryption programme TrueCrypt, which has not been developed any further since it was deemed insecure. So if a three-letter agency comes knocking at Open Whisper Systems' door, the developers around Moxie Marlinspike can tell the officials in good conscience where they can stick their wishes without immediately dropping a multi-million dollar business.
Ferner uses signal infrastructure that you already own. You don't get another key or another ID, but your phone number. This is particularly important for one of Signal's best features: SMS fallback. An example:
Because Signal wants everyone to use Signal, a message pops up on my screen giving me the option to send an SMS to my girlfriend and invite her to Signal. Even if she doesn't choose Signal, she knows a bit more about encryption.
You may not agree with my reasoning and that's okay. Because then you've done something that I advise all users to do: you've thought about encryption, compared products and made a conscious decision. And that's more than some people do. Take your knowledge, your curiosity and your critical reflection out into the world. Question everything that is loaded onto your phone and stay safe.
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all